Bypass Categories
Bypass Categories are similar to Custom URLs, except that they're used by agents to ignore something; for example, a domain, an IP range, a system process or SSL Interception. Bypasses are a powerful way to mitigate against applications that do not support proxying and to relax filtering where appropriate. The Web Security product supports a large number of Bypass types, but there are variations between desktop agents and gateway agent support, which are described in this section.
Bypass Type | Behaviour | Agent support | Example |
Bypass destination domain completely | Do not intercept HTTP or HTTPS traffic destined for the given domain | Windows, Mac, Gateway |
|
Bypass destination IP/CIDR completely | Do not intercept HTTP or HTTPS traffic destined for the given IP or CIDR | Windows, Mac, Gateway |
|
Bypass File Extension | Do not intercept HTTP or HTTPS traffic that has the specified file extension | Windows, Mac |
|
Bypass Executable/Process Name | Do not intercept HTTP or HTTPS traffic that is generated by the given executable or process (case sensitive, exact match) | Windows, Mac |
|
Bypass destination domain for SSL Interception | Do not intercept HTTPS traffic destined for the given domain | Windows, Mac, Gateway |
|
Bypass destination IP/CIDR for SSL Interception | Do not intercept HTTPS traffic destined for the given IP or CIDR | Gateway |
|
Bypass source IP/CIDR completely | Do not intercept HTTP or HTTPS traffic originating from the given IP or CIDR | Gateway |
|
Bypass source IP/CIDR for SSL Interception | Do not intercept HTTPS traffic originating from the given IP or CIDR | Gateway |
|
Bypass source IP/CIDR for user authentication | Do not authenticate HTTP or HTTPS traffic originating from the given IP or CIDR | Gateway |
|
Bypass user authentication for destination domain | Do not authenticate HTTP or HTTPS requests destined for a particular domain | Gateway - explicit proxy |
|
Bypass source MAC address for user authentication | Do not authenticate HTTP or HTTPS traffic originating from the given MAC address | Gateway ( |
|
Bypass HTTP Header | Do not intercept HTTP or HTTPS traffic if the specified HTTP header is matched | Windows, Mac |
The key e.g. Content-Type can contain The value e.g. application/json can contain |
Bypass with Proxy Exception | Add the bypass pattern to the macOS proxy exceptions list | Mac |
To bypass both the base domain and all sub-domains, add both patterns You cannot exceed 70 patterns or 650 characters across all patterns, whichever limit is met first. |
Bypass Types and behaviour
Managing Bypass Categories
To access the Bypass section, visit your USS Dashboard, and then click Products ⟶ Web Security ⟶ Bypass.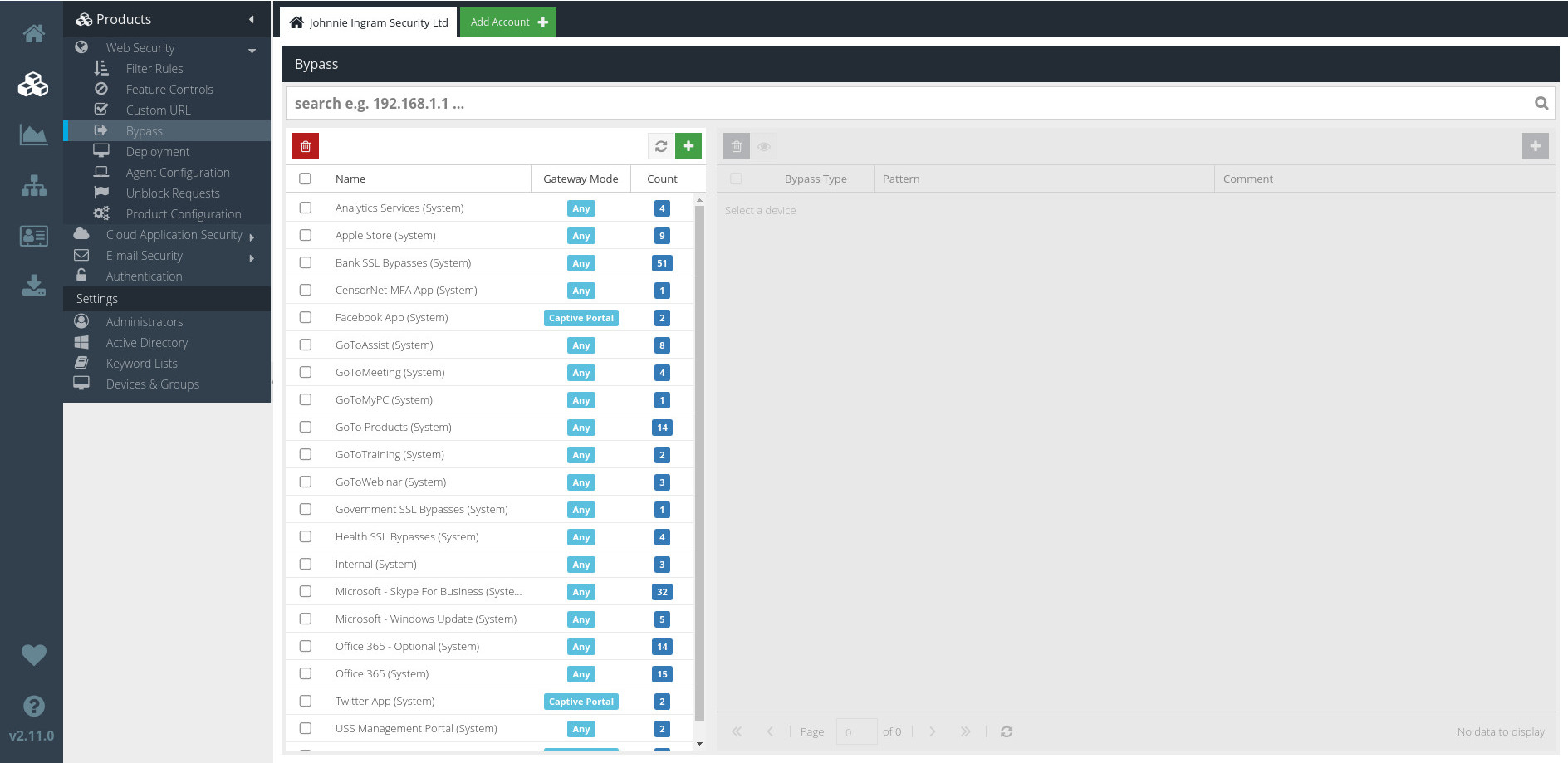
The list of current Bypass Categories is shown on the left. Click a Category to see the Bypass Patterns contained in the Category.
Searching Bypass Patterns
You can locate a specific Bypass pattern using the Search bar.
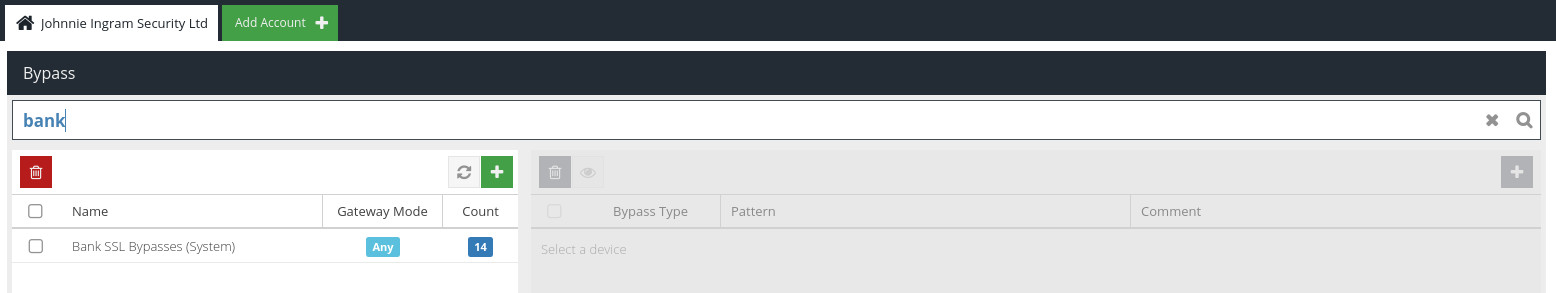
Enter your search query and click  (or just hit `Enter`). The Bypass list will now only show Bypasses containing a keyword pattern that matches your search query.
(or just hit `Enter`). The Bypass list will now only show Bypasses containing a keyword pattern that matches your search query.
To return to the full list of Bypasses, just click the  button.
button.
Adding a new Bypass Category
To add a new Bypass Category, click the  button, and enter details for the new Bypass in the form that's displayed.
button, and enter details for the new Bypass in the form that's displayed.
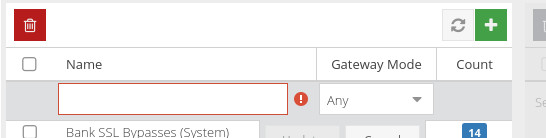
Name
Choose a name for the new Bypass.
Gateway Mode
The Gateway Mode dictates how and when the Bypass will function.
- Choose Direct Proxy to force SSL decryption and filtering on direct connections to the proxy on port 8080 (for example, via a browser configuration or WPAD).
- Choose Captive Portal to force SSL decryption and filtering on transparently-provided proxied connections (for example, Captive/Guest portal, WCCP, gateway mode).
- If you need the Direct Proxy and Captive Portal coverage, choose Any.
Click the  button to create the new Bypass Category.
button to create the new Bypass Category.
Editing Bypass Categories
To update a Bypass Category, simply double-click it. Once you've made any required changes, click  to save your changes.
to save your changes.
Deleting Bypass Categories
To delete a Bypass Category, just select it and click the  button.
button.
Managing Patterns
In the context of Bypass Categories, Patterns represent different domains, IP addresses, or ranges and processes as described in the Bypass Types table above.
Adding Bypass Patterns
To add a new Pattern, first select the Bypass Category to which the new Pattern should belong. Then, click the  button and enter the details in the form that's displayed.
button and enter the details in the form that's displayed.
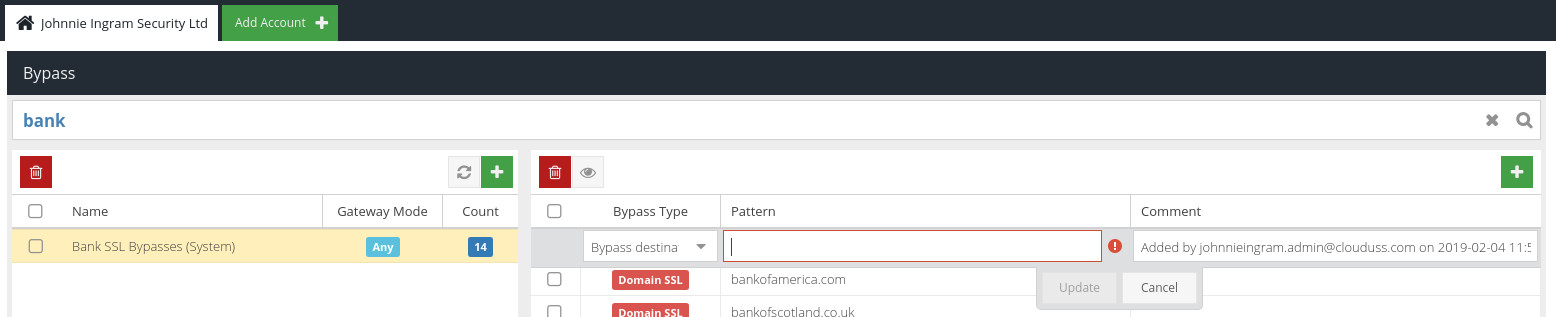
Bypass Type
The Bypass Type to use, as described in the Bypass Types table, above.
Pattern
The pattern against which to match. The pattern format will depend on the Type selected - see the Bypass Types table, above.
Comment
An optional comment or description about this Bypass pattern.
Click  to create the new Custom URL Pattern.
to create the new Custom URL Pattern.
Updating Patterns
To edit a Pattern, double-click it. Make the changes you require, and then click  .
.
Deleting Patterns
To delete a Pattern, select it and click the  button.
button.
Using Bypasses in Agent Profiles
Custom URLs can be used within Agent Configuration Profiles in order to bypass filtering for particular domains, IP ranges or processes. For example, you may want to add your company Intranet to a Bypass so that it is never filtered.