Analytics
The ASE product adds an ASE Event Activity report to the Analytics section.
Viewing Events
Navigate to Analytics and select ASE Event Activity to open the report.
Click Run Report to select the default timespan and return all events.
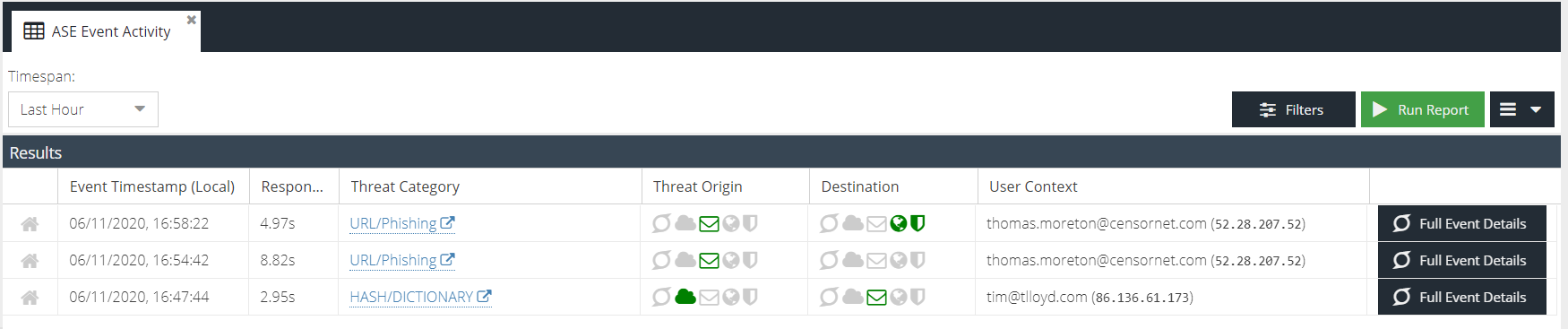
- The first column indicates whether the threat was part of the ASE ThreatShare community.
- Red 'share' icon - either thearc threat was shared with the community or contributed by the community to enhance protection.
- Grey 'home' icon - the threat was localised to your account only.
- Event Timestamp (Local) - the date and time of the event converted to your local time using your browser time zone offset. An additional (UTC) column is available by expanding the column header menu.
- Response - the time it took the ASE engine to process the threat once it had been received from the origin product. Units are milliseconds (ms), seconds (s) and minutes (min).
- Threat Category - the category of the threat as reported by the product where the threat originated.
- Threat Origin - the highlighted icon represents the product where the threat originated, e.g. Web Security, Email Security, etc.
- Destination - the highlighted icon(s) represent the product(s) that ASE sent the threat to as indicated in the configured ASE rules.
- User Context - details about the end user that triggered the threat. For example, email address, username or IP address.
- Full Event Details - opens the detailed Event Report for this particular event.
Searching for Events
To search for a specific event click the Filters button to expand the filter bar.
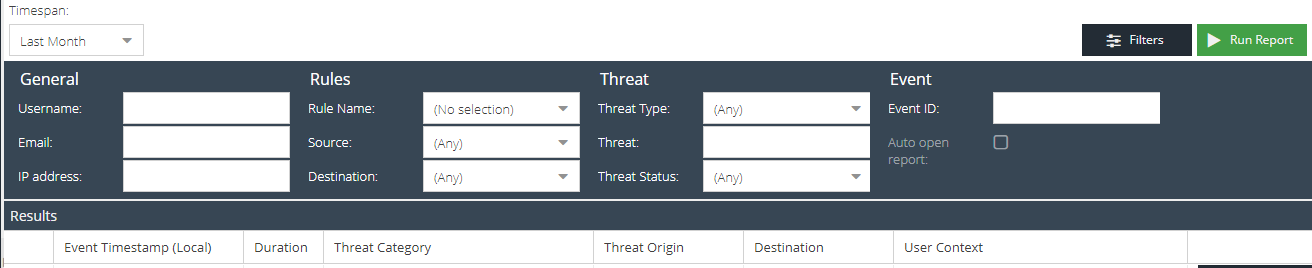
The available filters are:
General
- Username - search for a partial or exact username that appears in the User Context.
- Email - search for a partial or exact email address that appears in the User Context.
- IP address - search for a partial or exact IPv4 address that appears in the User Context.
Rules
- Rule name - the ASE rule that the event triggered.
- Source - product where the threat originated.
- Destination - the product(s) that ASE sent the threat object to.
Threat
- Threat Type - the type of threat object, e.g. URL, hash, IP.
- Threat - search for a partial or exact match on the threat object e.g. URL, hash, IP.
Event
- Event ID - specify an exact event ID from a notification to find the specific event.