Log Streaming to Microsoft Sentinel
The Log Streaming service allows enriched logs from the USS platform to be streamed to external services such as SIEM solutions, analytics platforms and SoC services. To request access to the Log Streaming service, please contact your service provider.
- Log in to the Microsoft Azure portal
- Navigate to Microsoft Sentinel
- Select your Microsoft Sentinel workspace
- Navigate to Configuration in the left hand menu, then Settings (at the bottom) and then Workspace settings tab
- Select the Agents option from the left menu
- Expand the Log Analytics Agent Instructions panel (for either Windows or Linux)
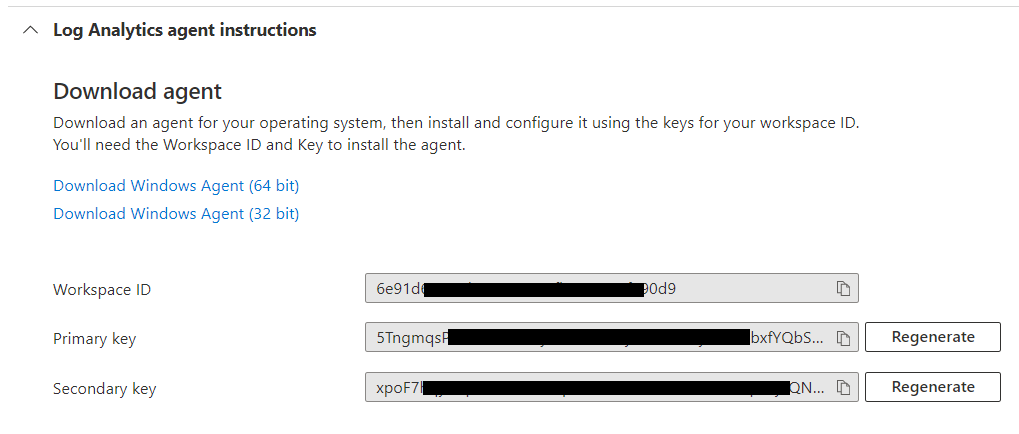
- Copy the Workspace ID and Primary Key and send them to service provider along with the name of the product(s) you wish to stream in to Microsoft Sentinel
- Wait for confirmation from your service provider that the log stream has been configured
- Navigate to Microsoft Sentinel again and select your Microsoft Sentinel instance and select Logs. Close any pop-up windows until you can see the Query editor
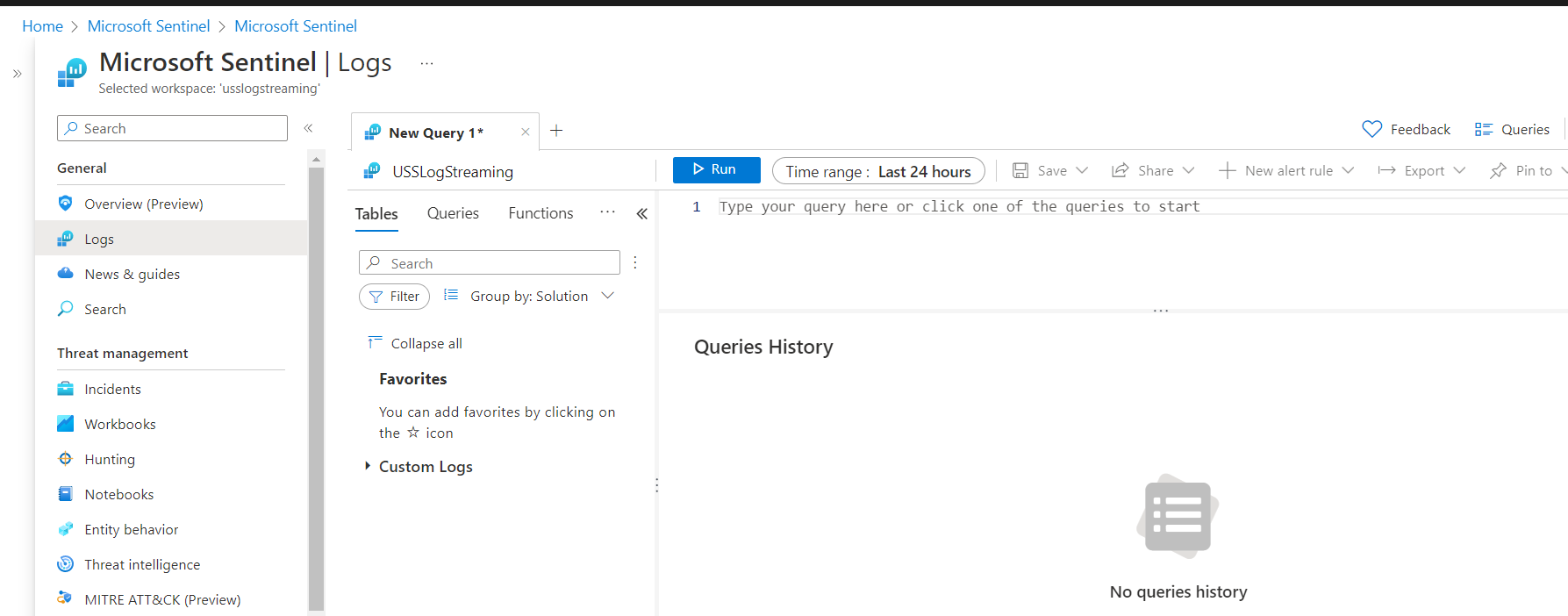
Once data is available, you should see a new table representing the streamed products under the Custom Logs expansion item. The table name will be in the format clouduss_<product_code>_CL (CL for "Custom Log" in Sentinel). If you are streaming multiple products or sub-logs of a product, each will have a separate table.
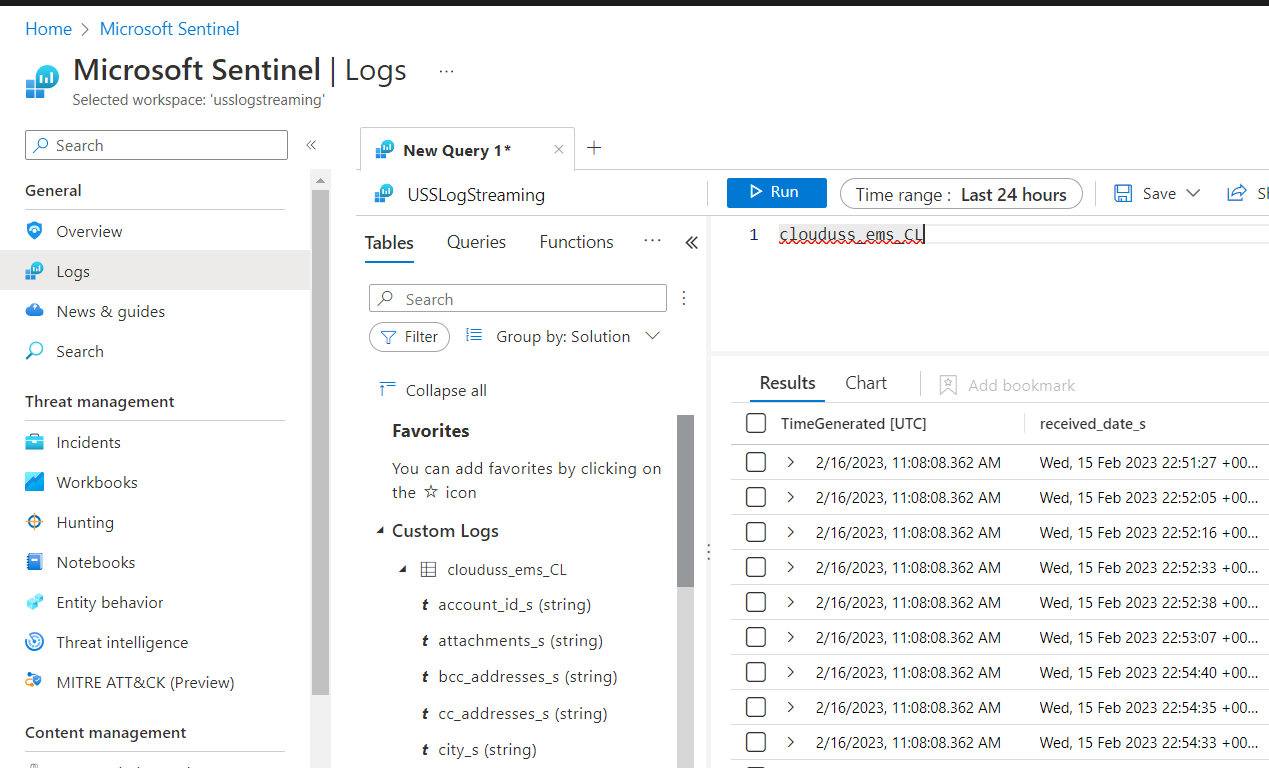
- The log stream is now set up and you can continue to query the data in Microsoft Sentinel.