Single Sign On
The dashboard can use Office 365 (Entra ID Directory) as a source for authenticating administrator users, meaning anyone with an approved Microsoft account can single sign on in to the dashboard. This is particularly useful for deploying the End User Portal.
Video guide.
This video will guide you through configuring configuring SSO on the USS Dashboard.
Step by Step guide.
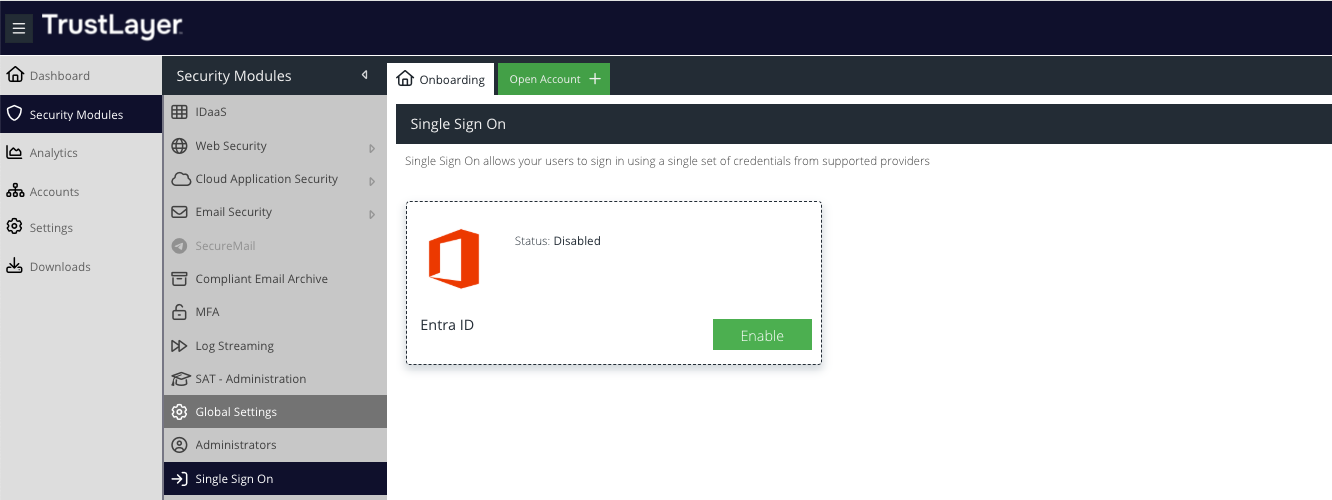
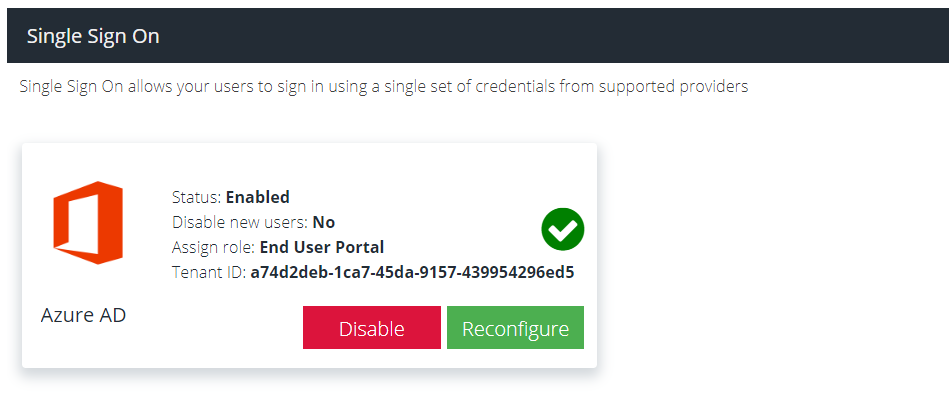
To enable, navigate to Security Modules -> Single Sign On and click the Enable button on the Entra ID tile:
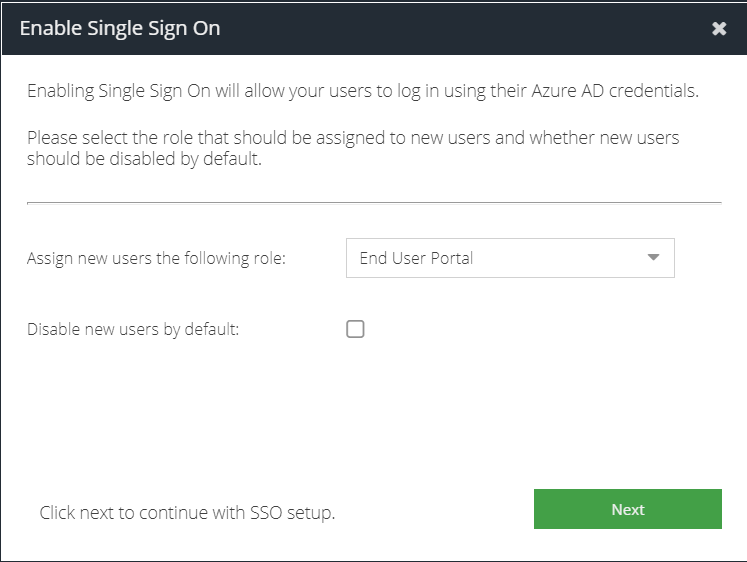
Assign new users the following role: select the role to apply to any new Entra ID users that sign-in. The role defaults to the least privileged; End User Portal. You can change this to be your preferred custom role however it is not possible to assign the Super User role at this stage. You can promote a user to a different role once they have signed-in for the first time using the Administrators section.
Disable new users by default: select this checkbox if you want to manually approve Entra ID users to access the portal. This will require unsuspending them using the Administrators section. This provides moderated access to the dashboard.
Click Next.
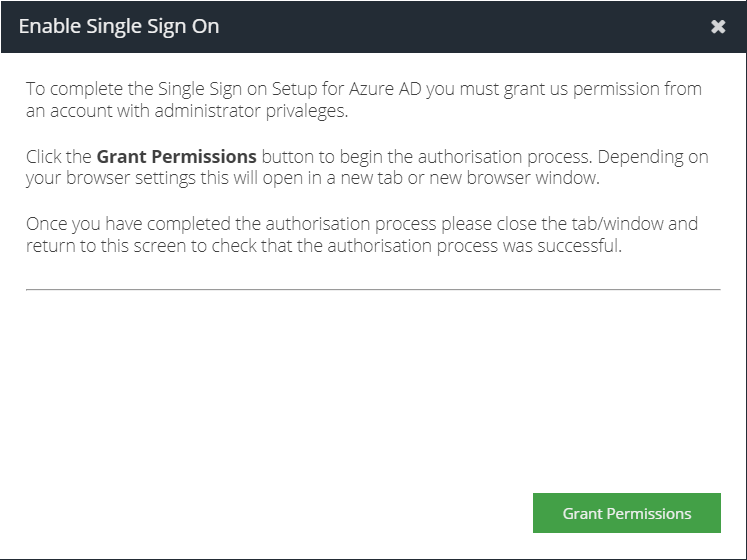
You must now sign-in with an administrator user from your Entra ID account and approve the consent. Click Grant Permissions to open the consent flow in a new browser tab.
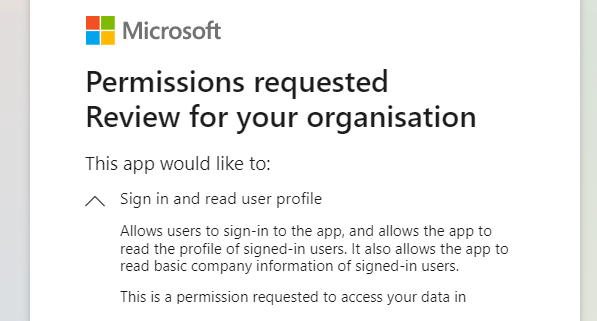
Click Accept. The Entra ID tenant will be approved for user authentication.
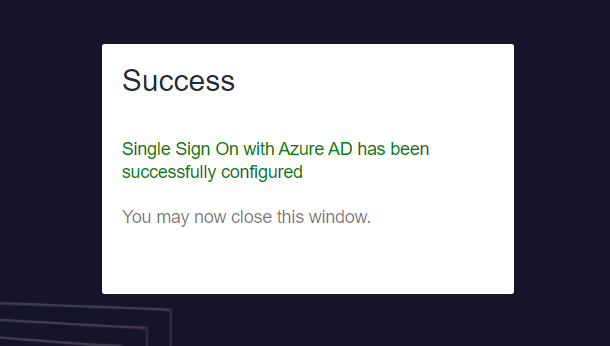
Close the tab to return to the Dashboard and view the Single Sign On status.
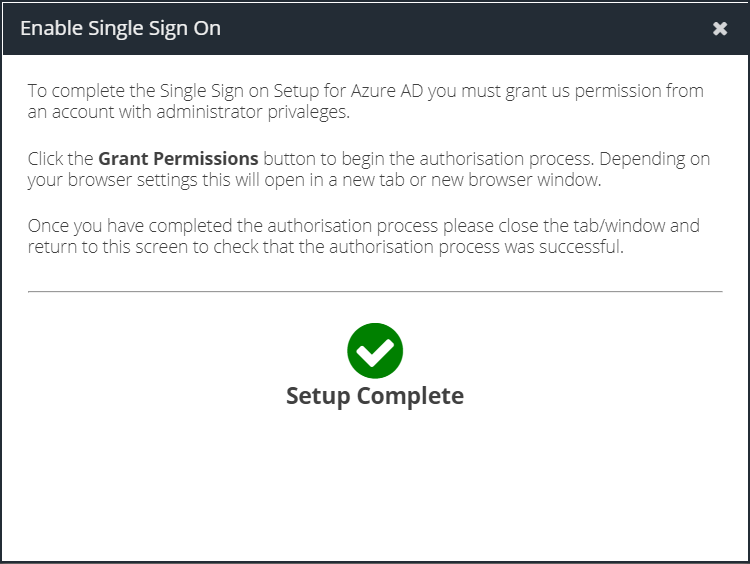
If you need to make changes to the assigned role you can Reconfigure at any time.
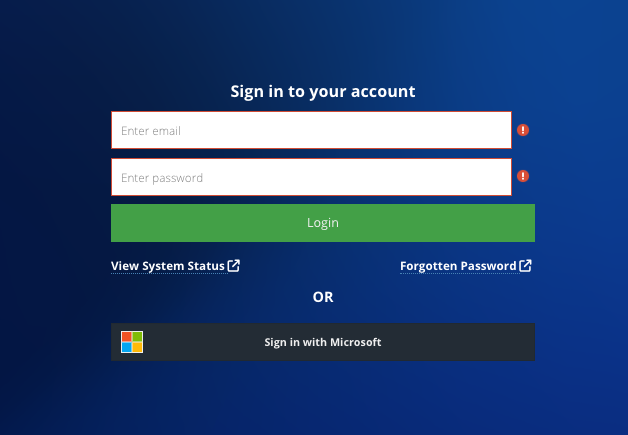
The setup is complete. Users can now sign in using the Sign in with Microsoft option on the dashboard login page:
Managing Single Sign-On Users
Once a user signs in using single sign on, their administrator account will have a Microsoft logo appended. This indicates the user is managed by Microsoft (Entra ID) for password and MFA.
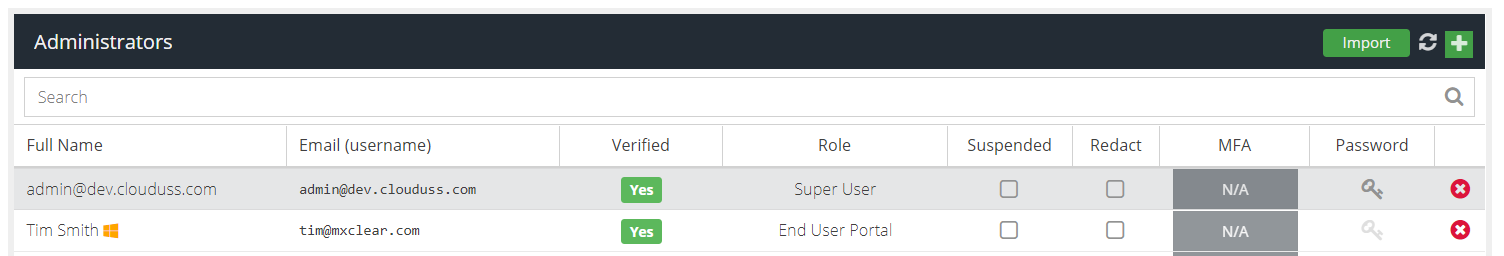
Administrators cannot change passwords or manage MFA for single sign on users.
Administrators can change the role of a single sign on user by double clicking the role name. Administrators can also suspend and unsuspend users.
Disabling Single Sign-On
Navigate to Products -> Single Sign On and click Disable
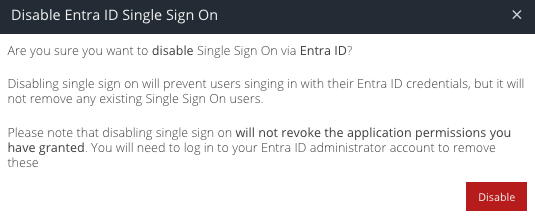
Click Disable again to confirm.
- Users that existed prior to Single Sign On being activated will be restored as non-Entra ID users
- Users that were created since Single Sign On was activated will no longer be able to sign in
Troubleshooting
Permissions Denied - E00009
You will need to troubleshoot using a non-Entra ID user, such as the primary @clouduss.com administrator for your account.
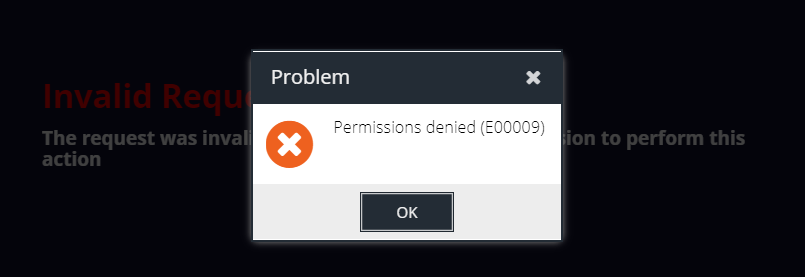
- Ensure that Single Sign On has been correctly activated on the account you are trying to sign in on by following the steps in this article
- Ensure that the username you are signing in as has been created in the Administrators view and is not suspended
- Ensure that the username you are signing in as does not belong to another account, for example, if you are performing an account migration
Need Admin Approval
This error means that your Entra ID administrator will need to grant consent for you to use the USS Auth application.
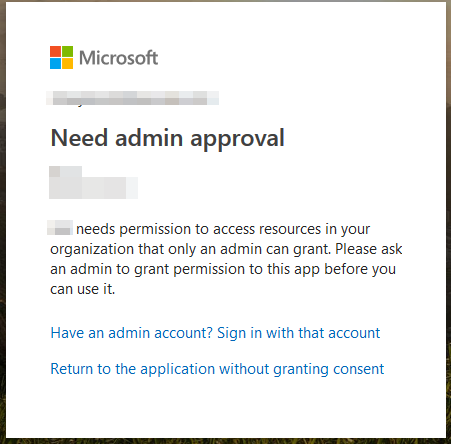
Log in to Entra ID as an administrator and navigate to Entra Directory -> Enterprise Apps -> select USS Auth -> Users & Groups and ensure the user that is trying to signed in has Default Access.
Permission Denied - E00010
The user is suspended in the Administrators section.