Rules
The ASE product has a number of pre-defined rules that aim to automate common tasks that a security analyst would often perform manually. The rules govern how threat objects will be shared between the core products that are licensed in your account.
The rules are centrally managed by the ASE product and require no configuration other than to enable them if required. Enabled rules can take preventative measures to stop threats from spreading by sharing the threat object detail, at machine speed, with other products that are able to use it.
Managing Rules
To manage rules, navigate to Products, ASE and then Rules.
Rules can be set to one of the following modes of operation:
- Disabled - the rule is not active. Matching threat objects will be ignored however they will still be logged in the Threats and Analytics sections.
- Notify Only - the rule is active and you will be notified via the configured Notification Settings if the rule is triggered. You can view the threat events that would have been shared had the rule been Enabled in the Product Sharing section. This area is for informational purposes only but will eventually offer the ability to release threats manually or remove them.
- Enabled - the rule is active and ASE will automatically share threat objects with related products as per the rule description. Additionally, any configured recipients will be notified.
Configuring Notifications
To add a recipient to receive notifications for a rule:
- Click the cog (settings) icon next to the rule name to open the notifications panel
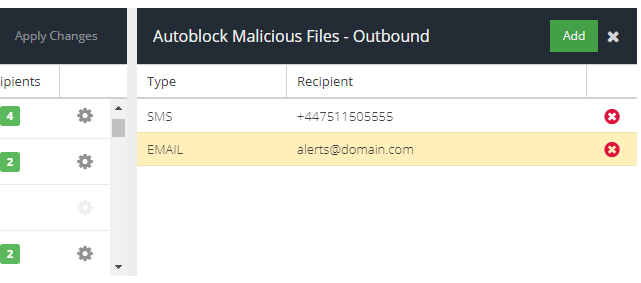
- Click the Add button
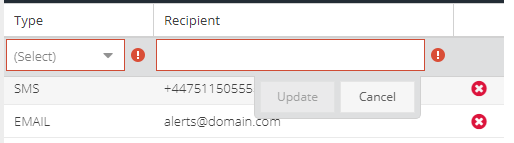
- Select the type of notification, which can be SMS or Email and then the corresponding recipient phone number (including internationally code) or email address.
- Click Update
The next time the rule is triggered the recipient(s) will receive a notification containing a link to the event report.
To edit a recipient that receives notifications for a rule double click the entry in the notifications list.
Receiving Notifications
The first time a threat is detected and a rule matches, a notification will be sent in real time based on the Notification Settings attached to the rule. Further notifications for the same threat will then be summarised for up to one hour after the initial threat detection, with an update sent every 5, 10, 20, 40 and 60 minutes. If the threat continues to be seen after one hour, the process will start again.
The notification will summarise the event and contain a link to open a more detailed Event Report. An example email notification is below:
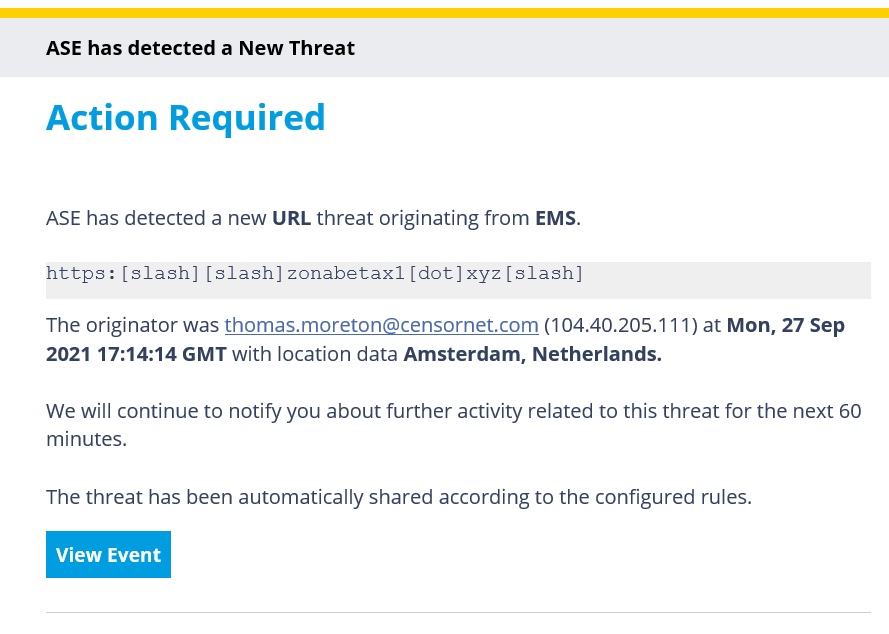
The email notification will attempt to summarise the threat, the originator, geo-location and provide a link to a detailed Event record in the dashboard. SMS based notifications have limited space, so will contain less information but may be more convenient to receive.
An example SMS notification: