Email Security: Quick Start for Google Workspace
- Email Security: Quick Start for Google Workspace
- Preparing The Environment
- Configure EMS for Gmail using Google Workspace accounts
- Configuring Inbound Mail
- User Directory - Mailbox Synchronisation.
- Configure Inbound mail on Gmail using Google Workspace to reject non-EMS emails.
- Post MX record change
- Configure Outbound mail on Gmail using Google Workspace to send Email via the EMS servers
- Configure Google Workspace to bypass EMS for Internal mail
Email Security: Quick Start for Google Workspace
Email Security: Quick Start for Google Workspace
Follow this guide to successfully deploy Email Security (EMS) for Google Workspace.
Preparing The Environment
You will receive a provisioning email outlining the account activation for Email Security. At this point, you can log in to your USS Dashboard and see the EMS product listed alongside your other Cloud USS products.
The below steps will guide you through the configuration needed for EMS to protect your Google Workspace environment.
Configure EMS for Gmail using Google Workspace accounts
Configuring Inbound Mail
- Navigate to Products ⟶ E-mail Security ⟶ Product Configuration ⟶ Inbound Email.
- Click + to add a new Delivery Route.
- In the Domain field, select the domain you wish to configure.
- In the Route field, enter
ASPMX.L.GOOGLE.COMwith a cost of5. - Repeat steps 2 to 4 to add the remaining routes:
ALT1.ASPMX.L.GOOGLE.COM
- The final routes should look similar to the screenshot below:
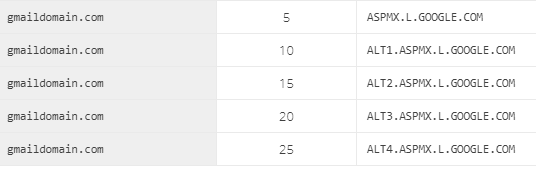
User Directory - Mailbox Synchronisation.
This step shows you how to set up Google Workspace integration to add email addresses to EMS dynamically.
KB Link Here: https://help.clouduss.com/settings/google-workspace-synchronisation
Configuring Outbound Mail
- Navigate to Products ⟶ E-mail Security ⟶ Product Configuration ⟶ Outbound Email.
- Click + to add a new Sending Host.
- Enter
spf://_spf.google.comas the new Hostname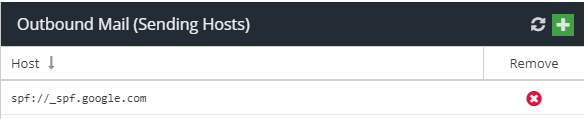
Configure Inbound mail on Gmail using Google Workspace to reject non-EMS emails.
You should configure GMail using Google Workspace to block any inbound email that does not originate from the Email Security (EMS) product. However, you will need to do this via a two-step process. This section is split into two sections – prior MX record change and post MX record change.
Prior to changing MX records
Before changing MX records it is recommended that the Email Security IP addresses are added to the inbound gateway so that when MX records are changed all messages are not quarantined.
The steps below explain this process.
- Log in to the Google Workspace Admin Console with an administrator account.
- Click on the square dots icon, then Admin -> Apps and then Google Workspace
- Click on GMail to take you to Settings for Gmail.
- Scroll down to Spam, phishing, and malware and configure/edit the Inbound Gateways.
- Add a Name to the Inbound setting, for example, “Email Security" if not already configured.
- Add the IP addresses for our service and click Save.
Use the link below to determine the EMS IP Addresses required for your environment.
KB Link Here: https://help.clouduss.com/ems-knowledge-base/mx-records-and-ip-addresses-for-all-regions - The entries should look like this if using the EU servers (NOTE: ensure you DO NOT click Reject all mail not from gateway IPs)
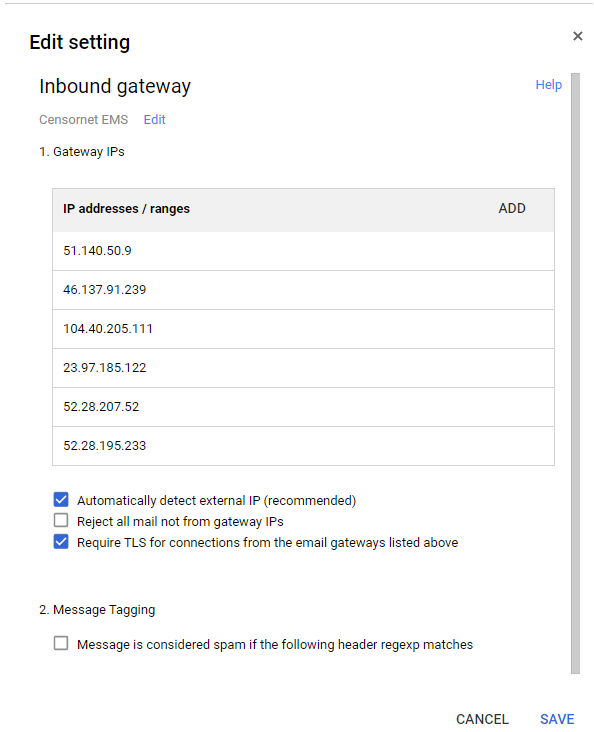
- Click on Message is considered spam if the following header regex matches and select the options below:
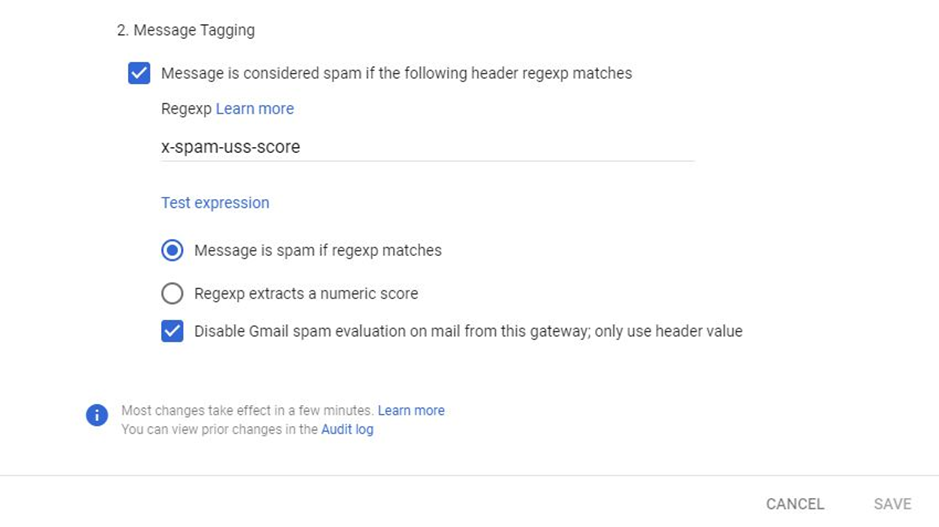
- At the bottom of the Advanced Settings page, click Save to apply the changes.
- Ensure that this configuration is replicated to Google Workspace before changing any MX records.
- Configuring MX Change.
Use the link below to determine the required MX Records required for your environment.
KB Link Here: https://help.clouduss.com/ems-knowledge-base/mx-records-and-ip-addresses-for-all-regions
Post MX record change
Once MX records have been changed and replicated to the internet, email should start flowing through the Email Security product. You can verify this via the Email Security Activity reports and charts. You can also check this in the Google Workspace portal by following these steps:
- Log in to the Google Workspace Admin Console with an administrator account.
- Click on the square dots icon, then Admin -> Apps and then Google Workspace
- Click on GMail to take you to Settings for Gmail.
- Click on Setup.
- Check that the MX records match the below:
Use the link below to determine the required MX Records required for your environment.
KB Link Here: https://help.clouduss.com/ems-knowledge-base/mx-records-and-ip-addresses-for-all-regions
- Scroll down to Spam, phishing, and malware and configure/edit the Inbound Gateways
- Tick the Reject all mail not from gateway IPs checkbox
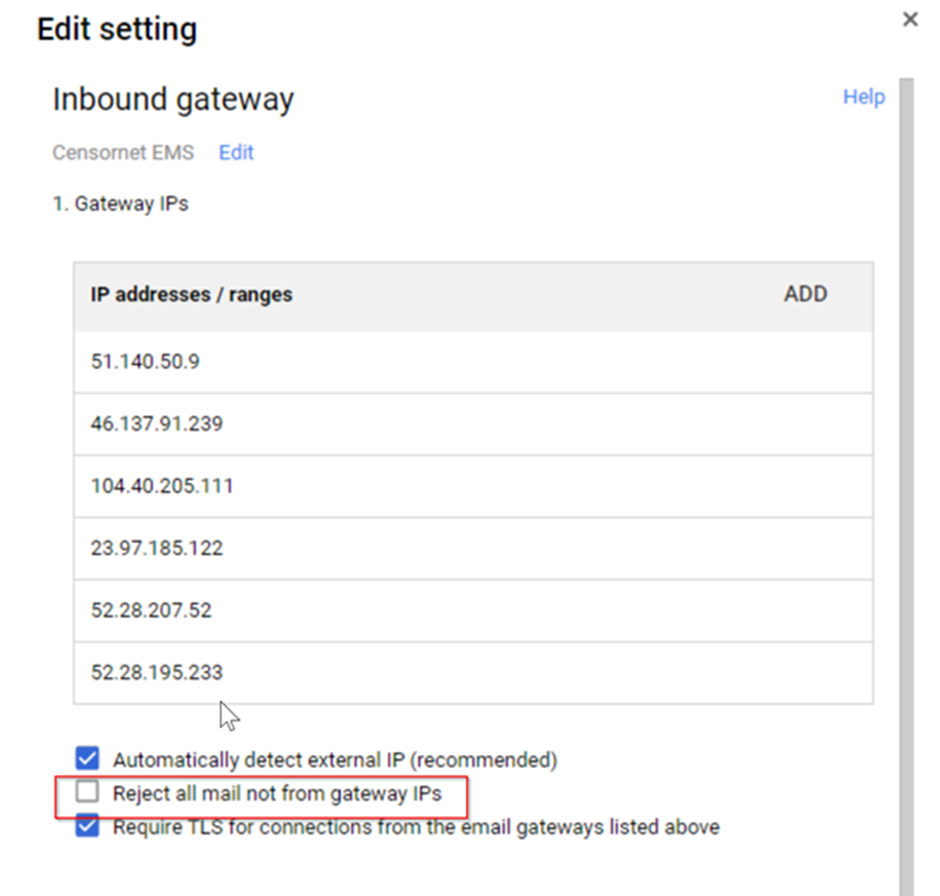
- Click Save
Configure Outbound mail on Gmail using Google Workspace to send Email via the EMS servers
To configure outbound email for GMail using Google Workspace you will need to login to the GMail using Google Workspace Admin console. As we use two smart hosts you will need to route the outbound email via a host and rule. Here are the details required to configure outbound email to the Email Security product:
- Login to the Google Workspace Admin Console with an administrators account.
- Click on the square dots icon, then Admin -> Apps and then Google Workspace
- Click on GMail to take you to Settings for Gmail.
- Click on Hosts section.
- Click the Add Route button.
- Give the route a Name like “EMS Outbound”
- In the Specify Email server select Multiple hosts.
- Add a primary entry for each of the outbound servers, for example, for the EU region:
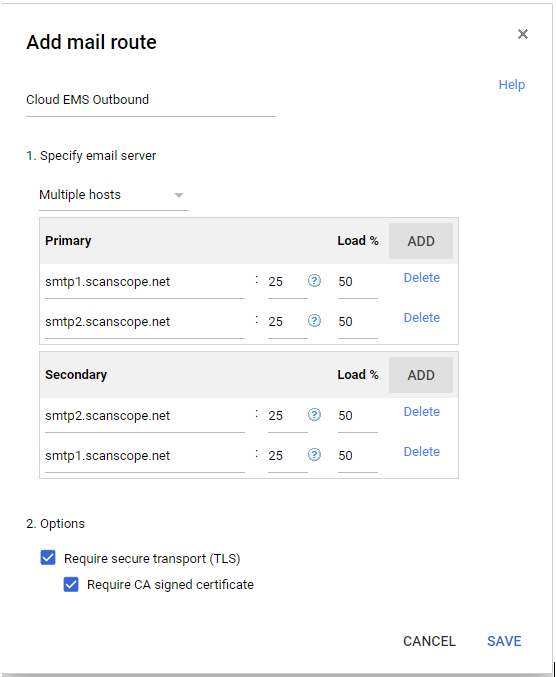
Use the link below to determine the required route for your environment.
KB Link Here: https://help.clouduss.com/ems-knowledge-base/mx-records-and-ip-addresses-for-all-regions
- Click Save
- Navigate to Advanced section from Settings for Gmail and scroll down to the Routing setting in the Routing section
- Click configure for Routing. This will open up a new Add setting option.
- Enter a name like “EMS Outbound Rule”
- Select the checkbox for Outbound in Messages to affect. (section 1)
- Select Change route in For the above types of messages, do the following. (Section 3)
- Change the Normal routing to "EMS Outbound Rule" created above. (Section 3)
- (Optional) Under Encryption (onward delivery only), check the Require Secure Transport (TLS) option
- Click Add Setting button or, if editing an existing configuration, click Save.
- At the bottom of the Advanced Settings page, click Save.
Configure Google Workspace to bypass EMS for Internal mail
- Login to the Google Workspace Admin Console with an administrators account.
- Click on the square dots icon, then Admin -> Apps and then Google Workspace
- Click on GMail to take you to Settings for Gmail.
- Click on Hosts section.
- Click on the Add Route button
- Give the route a Name like “Google Internal”
- In the Specify Email server select Multiple hosts.
- Add a primary entry for each of the GMail Servers listed below:
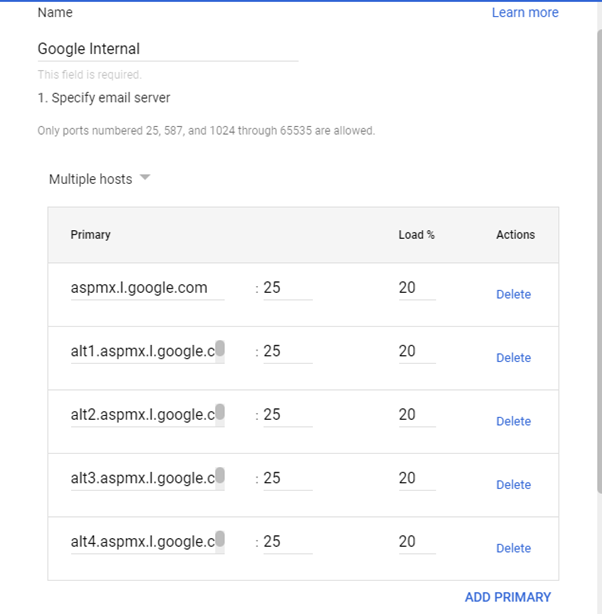
aspmx.l.google.com
alt1.aspmx.l.google.com
alt2.aspmx.l.google.com
alt3.aspmx.l.google.com
alt4.aspmx.l.google.com
- Click Save
- Navigate back to Settings for Gmail and scroll to the Routing setting in the Routing section
- Click on Add Another for Routing. This will open up a new Add setting option.
- Enter a name like “Internal Route”
- Select the checkbox for Internal – Sending in Messages to affect.
- Select “only affect specific envelope recipients” by selecting Show Options -> Envelope Filter and define a REGEX for your internal domain(s)
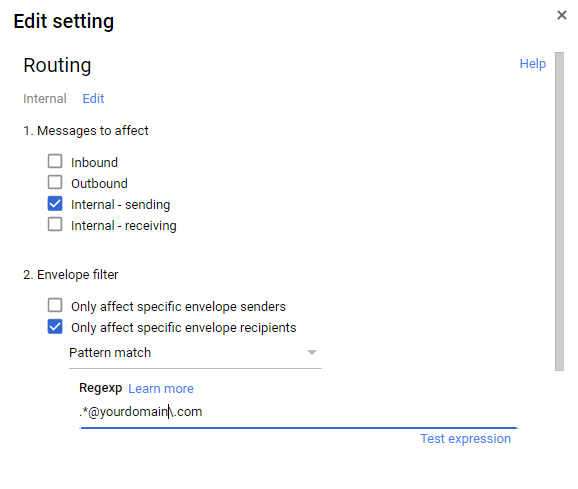
NOTE: For multiple domains, you can add them into the regex in the format of .*@firstdomain\.com|.*@seconddomain\.co\.uk, for example:
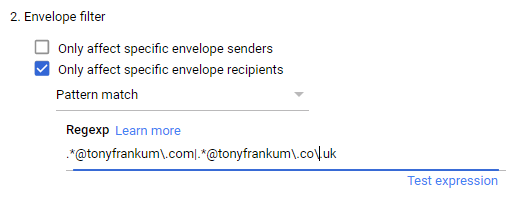
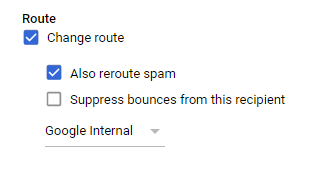
- Select Change route in For the above types of messages, to do the following.
- Change the Normal routing to "Google Internal" created above.
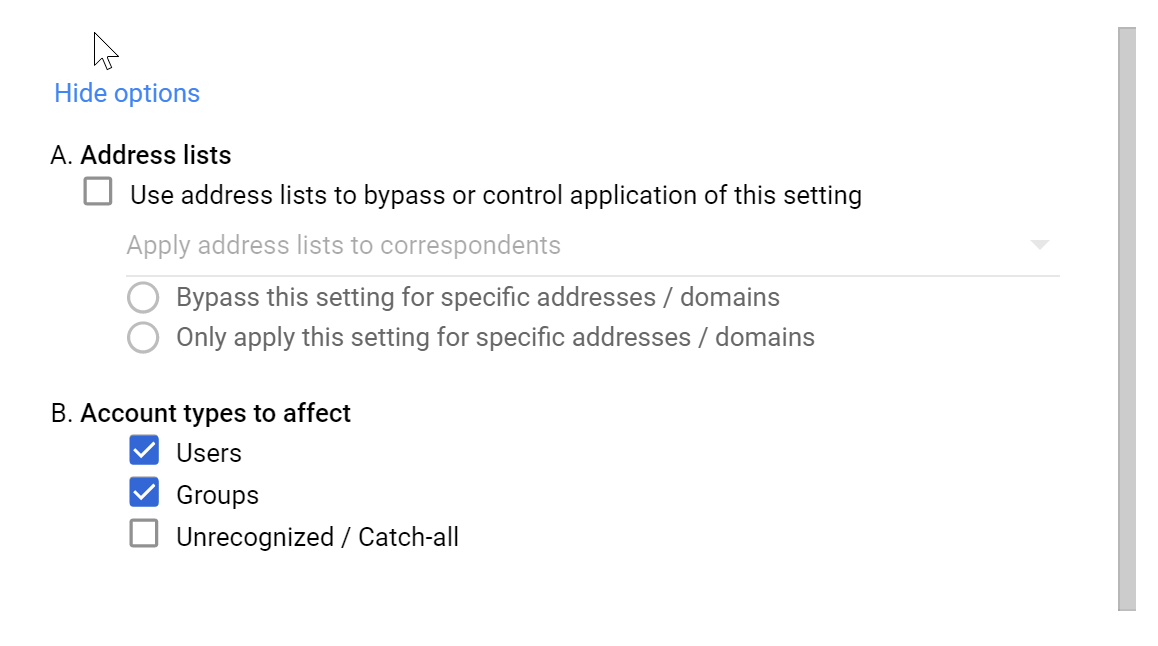
- Click on Show Options at the bottom of this page and Select “Users and Groups” in the Account types to affect
- Click the Add Setting button, and click Save.
- At the bottom of the Advanced Settings page, click Save.
Now all internal mail is routed directly to Google servers, and all other mail routes through the Email Security Outbound Gateway.