EMS - Message Rules
- Managing rules
- Creating a new Rule
- Conditions
- Attachment Name
- Body
- Body or Subject
- Core Service
- Direction
- DKIM Enabled
- DKIM Signature
- DMARC Failure
- DMARC Policy
- Domain Threat Level
- E-mail Size
- Executive Tracking
- Fake Sender Headers
- File Type
- Group Membership
- Header Exists
- IP Reputation
- Mailbox Exists
- Message Security
- MX Record
- Nearby Domains
- Own Domain
- Protected Attachment
- ASE Lookup (requires ASE license)
- Recipient
- Recipient Count
- Sender
- Sender in List
- Sending Domain MX Record
- Spam Score
- SPF
- Strip and Replace
- Subject
- URL Scanner
- Virus Ruleset
- Virus Score
- Actions
- Add Message Header
- Add to Spam Score
- Add to Virus Score
- Append HTML
- Append Text
- Append to Subject
- Archive (Backup)
- DKIM Signing
- DKIM Verification Required
- LinkScan
- Notify Recipient
- Notify Sender
- Prefix HTML
- Prefix Text
- Prefix to Subject
- Publish to ASE (requires ASE license)
- Re-Route To
- Save Copy in Quarantine
- Send Copy To
- Set Spam Score
- Set Virus Score
- Subtract from Spam Score
- Subtract from Virus Score
- Final Actions
- System rules
The Email Security Message Rules engine lies at the heart of your email security process. The powerful rule builder gives you precise control of the email traffic going to and from your domain. To take full advantage of Email Security, you should set up a series of cascading Rules.
Managing rules
To see the Rules currently in place for your Email Security account, visit your Dashboard and click Security Modules ⟶ Email Security ⟶ Message Rules.
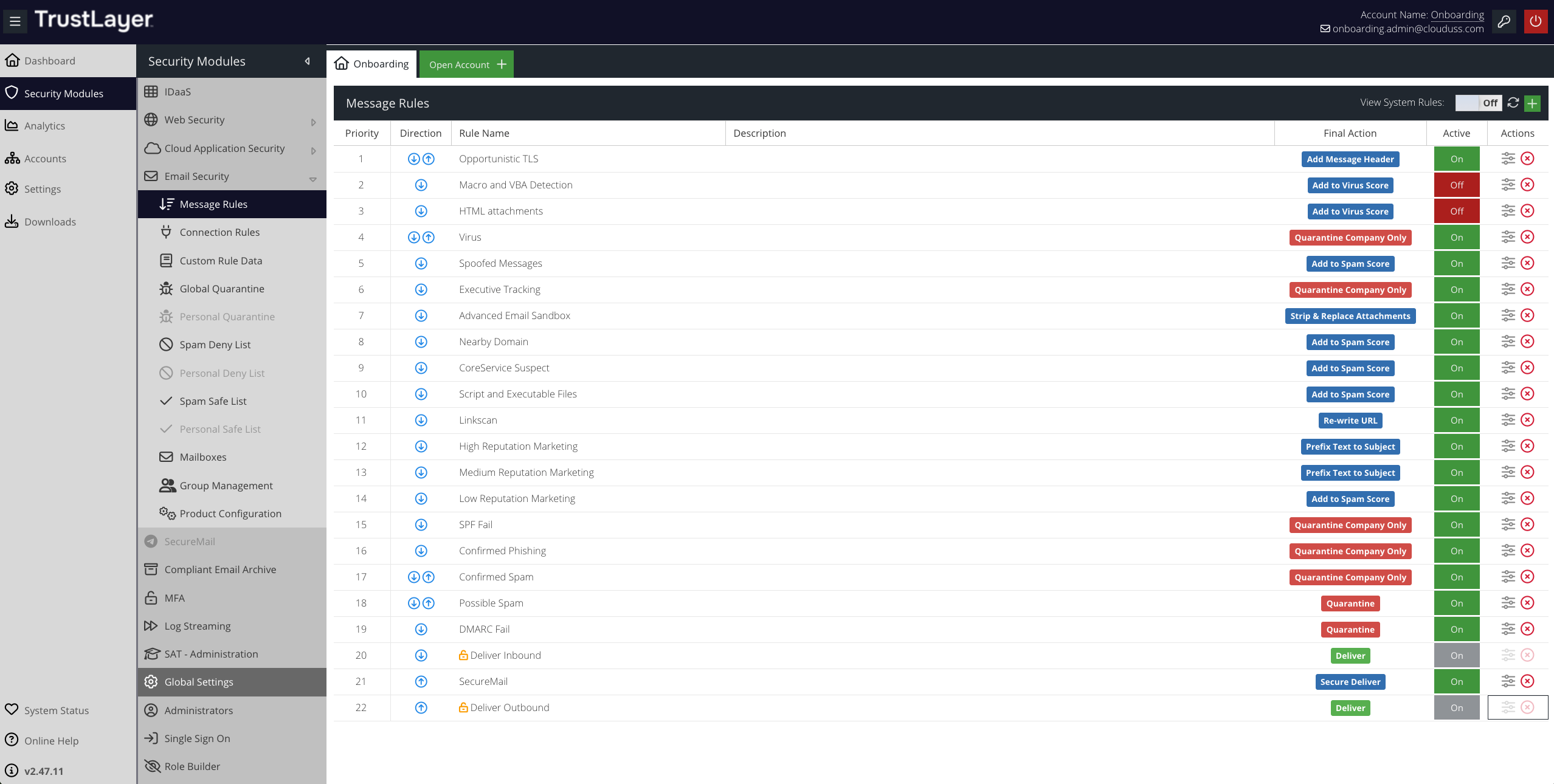
Rules priority
Message Rules are processed in order as they appear on the Message Rules screen. So, the Rule at the top of the list (with the Priority of 1) will be executed first.
If an email triggers a Rule with an Action but no Final Action, subsequent Rules will still be processed against that email. Processing only stops when an email triggers a Rule which has a Final Action. Once a Final Action is encountered in any Rule, no further Rules will be processed for that email. The Final Actions are:
- Quarantine
- Quarantine - Company
- Delete
- Deliver
Direction
A Rule may be processed only against incoming mail, only against outgoing mail, or against both incoming and outgoing mail. The Direction column indicates when the Rule will be processed.
 | This Rule will only be processed against incoming email. |
 | This Rule will only be processed against outgoing email. |
 | This Rule will be processed against incoming and outgoing email. |
Re-ordering message rules
To change the order in which your message Rules are processed, simply left-click a Rule in the list, and drag it to a new position.
Deleting a message rule
To delete a Rule, click the  icon next to the Rule you want to delete.
icon next to the Rule you want to delete.
You can also delete a Rule within the Rule Builder window by clicking  .
.
Editing a message rule
To edit a Rule, double-click it in the list. The Rule Builder will open.
image the Rule Builder window.
Make any changes you wish, and then click  .
.
Inactive rules
A Rule can be set to be inactive. An inactive Rule will never be triggered, and will not be included in email processing at all. You can easily see which Rules are inactive in the Message Rules window, where the Active column will list each rule as being either  or
or  .
.
To change the active status of a Rule, double-click the Rule to edit it, and then check or uncheck the Active checkbox.
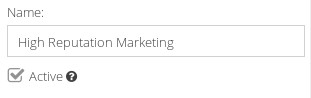
Creating a new Rule
To create a new Rule, click the  icon. Give your new Rule a sensible name, and click
icon. Give your new Rule a sensible name, and click  .
.
The Rule Builder Window will be displayed.
Name
If you want to rename your new Rule, enter a new name here.
Active
Newly created Rules are inactive by default. To set your new Rule as active, enable the checkbox.
Conditions
You can apply one or more Conditions to your Rule. Each condition limits the emails that this Rule will match.
Attachment Name
The Condition will match if the email has an attachment, and the attachment fulfils the conditions you specify (from the drop-down list). For example, attachments with a double file extension (such as PretendingNotToBeMalicious.docx.exe) or attachments with macro extensions for Office.
Body
The Condition will match if the body of the email matches the specified Condition Value. For example, if the email body contains sexual explicit or homophobic content.
Body or Subject
The Condition will match if the body of the email or the email's subject matches the specified Condition Value. For example, if the email subject features known spam blog URLs, or if the email body contains sexual explicit content.
Core Service
The Condition will match if the email's reputation (as determined by the core anti-spam service) meets the value specified in the Condition Value.
Direction
Choose whether this Rule should be run against inbound email (mail coming in to addresses on your server) or outbound email (mail sent by users on your server).
DKIM Enabled
The Condition will match if DKIM (DomainKeys Identified Mail) is enabled on your server.
DKIM Signature
The Condition will match if the DKIM (DomainKeys Identified Mail) signature for the email matches the Condition Value.
DMARC Failure
The Condition will match if the DMARC (Domain-based Message Authentication, Reporting and Conformance) failure action from the remote DNS record matches the Condition Value. You will usually want to set this Condition to "Match type: Matches" and "Condition Value: Reject".
DMARC Policy
The Condition will match if the DMARC (Domain-based Message Authentication, Reporting and Conformance) policy result matches the Condition Value.
Domain Threat Level
If a Domain Threat Level Condition is added to a Rule, Email Security will scan domains within the header and envelope fields of the email, using leading threat intelligence fields, to identify high-risk domains.
E-mail Size
The Condition will match if the email's total size matches the specified Condition Value. For example, if the email size is less than 4kb, or if the email size is greater than 20mb.
Executive Tracking
If an Executive Tracking Condition is added to a Rule, Email Security will scan headers for attempts to impersonate company executives, or to obtain sensitive information from high-profile employees (so-called "whale phishing" attacks).
You can activate executive tracking for specific Active Directory groups on the Group Management screen.
Exact, High or Medium. This value represents the amount of variation that the Condition will tolerate. For example, the Exact value will only trigger on an exact match, whereas High would trigger if one character had been changed to a number in the label name. We recommend setting the Condition to High by default, to avoid false positives.Fake Sender Headers
Use this Condition to check whether the email sender headers have been forged.
File Type
Use this Condition to check if the email contains an attachment of the specified file type.
Group Membership
Use this Condition to check if the email mailbox belongs to a specific synchronised Active Directory group.
Header Exists
Use this Condition to check if a specific header or header value exists within the message using Custom Rule Data.
IP Reputation
Use this Condition to check if the IP address of the email's originating server matches a specified reputation value.
Mailbox Exists
Check whether the mailbox to which the email is addressed exists on your server.
Message Security
Use this Condition to check if the email is digitally signed or encrypted.
MX Record
Use this Condition to check that the hostname in the MX records responds to an SMTP request.
Nearby Domains
Adding this Condition will allow Email Security to scan the email headers for addresses that include domain names similar to your legitimate domain name (whitehouse.com rather than your legitimate domain name of whitehouse.gov, for example). Cousin domains, as these nearby domain names are also called, can often be an indication of a malicious or spam email.
Own Domain
Use this Condition to check if the sender of the email is configured as a domain for your account.
Protected Attachment
You can use this Condition to check if the email has an attachment which is password-protected (zip and PDF currently supported).
ASE Lookup (requires ASE license)
Use this condition to send elements of the email to ASE to determine if they are known to ASE Threat Intelligence. This is typically used as a local loop-back to quarantine emails that contain elements known to ASE as being a threat. Options are:
- URLs in Body - up to 400 URL's from the message body will be extracted
- Sender IP - the IP address of the sender
- Sender Domain - the domain name of the sender
- Attachment Hash - a SHA256 hash of each file attachment (see list of supported formats)
ASE will check if the threat is known to your account already and also if it is known to the ThreatShare community. You can configure Match or Does Not Match logic to the result.
Recipient
This Condition can be used to test against the email's recipient. You can check whether the recipient appears in your Active Directory export, or you can test against any Custom Rule Data you have created.
Recipient Count
The Condition will match if the email's total number of recipients matches the specified Condition Value.
Sender
Use this Condition to check whether the sender of the email matches a specific pattern.
Sender in List
Use this Condition to check whether the sender of the email is in a specific list (usually the Safe List or the Deny List).
Sending Domain MX Record
Use this Condition to check that the originating domain for the email has a valid MX record.
Spam Score
The Condition will match if the email's spam score (as calculated by Email Security) matches the specified Condition Value.
You can use Rule Actions such as Add to Spam Score, Set Spam Score or Subtract from Spam Score to adjust the score.
SPF
This Condition checks the Sender Protection Framework score for the email's domain.
Strip and Replace
Used specifically for the Sandbox feature. It removes and replaces attachments with a text file.
Subject
The Condition will match if the email's subject matches the specified Condition Value. For example, if the email subject features known spam blog URLs.
URL Scanner
The URL Scanner Condition will scan any links in the email message body, looking for known threats. You can choose to either match Clean URLs or Threat URLs.
Virus Ruleset
This Condition can be used to detect the presence of malware, in macros, VBA scripts or Office documents. The Condition checks against a given certainty value - either greater than or less than.
Virus Score
This Condition will trigger if the email has a Virus Score matching the value you set.
Actions
Use Actions to tell Email Security what to do with an email that matches the Conditions you've already set on the Rule.
Add Message Header
Adding this Action to a Rule will instruct Email Security to add a custom header to the email. You can enter any value you like. For example, HX-Clacks-Overhead: "GNU Terry Pratchett"
Add to Spam Score
Add this Action to a Rule to increase the email's spam score by the specified amount. The spam score can be used by the Spam Score Condition to perform further actions.
Add to Virus Score
Add this Action to a Rule to increase the email's virus score by the specified amount. The virus score can be used by the Virus Score Condition to perform further actions.
Append HTML
Append a fragment of HTML to the body of the email. You can use the rich-text editor to enter and format your HTML.
Append Text
Append a fragment of plain text to the body of the email.
Append to Subject
Append the text of your choice to the email's subject.
Archive (Backup)
Store the message in the Backup Archive.
DKIM Signing
Sign the message with a DKIM signature. You can choose the key complexity value from the drop-down list.
DKIM Verification Required
Specify the type fo DMARC verification required to result in a pass.
LinkScan
Email Security's LinkScan functionality allows you to apply on-demand link scanning to URLs in the email message body. You can choose the behaviour if a potential threat is detected, from the drop-down list.
Notify Recipient
Send a message to the recipient of the email. You can configure the sender address, subject, and body of the email message that is sent.
Notify Sender
Send a message to the user that originally sent the email. You can configure the sender address, subject, and body of the email message that is sent.
Prefix HTML
Add a fragment of HTML to the start of the email's body text. You can use the rich-text editor to enter and format your HTML.
Prefix Text
Add a fragment of plain text to the start of the email's body text.
Prefix to Subject
Add the text of your choice to the start of the email's subject.
Publish to ASE (requires ASE license)
Determine what element of the email will be published to ASE for further analysis. This is typically used with other conditions to match suspicious emails and an action to quarantine. Options are:
- URLs in Body - up to 400 URL's from the message body will be extracted and publishes to ASE for further analysis
- Sender IP - the IP address of the sender
- Sender Domain - the domain name of the sender
- Attachment Hash - a SHA256 hash of each file attachment (see list of supported formats)
Re-Route To
Re-route the email to a specific email address.
Save Copy in Quarantine
Save a copy of this email to the Global Quarantine.
Send Copy To
Send a copy of this email to another recipient as a BCC.
Set Spam Score
Use this Action to set the email's spam score to a specific value. The spam score can be used by the Spam Score Condition to perform further actions.
Set Virus Score
Use this Action to set the email's virus score to a specific value. The virus score can be used by the Virus Score Condition to perform further actions.
Subtract from Spam Score
Add this Action to a Rule to decrease the email's spam score by the specified amount. The spam score can be used by the Spam Score Condition to perform further actions.
Subtract from Virus Score
Add this Action to a Rule to decrease the email's virus score by the specified amount. The virus score can be used by the Virus Score Condition to perform further actions.
Final Actions
Use Final Actions to determine what will ultimately happen to an email that's triggered your Rule. Unlike standard Actions, any Final Action added to a Rule will stop the processing of any subsequent Rules for this email.
You can only add one Final Action to a Rule.
Quarantine
This Final Rule moves the email to the Quarantine area. The email will not be delivered.
Quarantine - Company
This Final Rule moves the email to the Company Quarantine area. The email will not be delivered.
Delete
This Final Rule permanently deletes the email. The email will not be delivered.
Deliver
This Final Rule allows the email to be delivered normally.
System rules
Your Email Security installation comes with a number of out-of-the-box System Rules, provided by your Service Provider. These System Rules are intended to give a good set of initial base rules, that will protect a typical email system from most threats. System Rules cannot be changed, although you can of course override them with your own Rules.
System Rules are not shown in the Message Rules window by default. To display them, click the  toggle.
toggle.
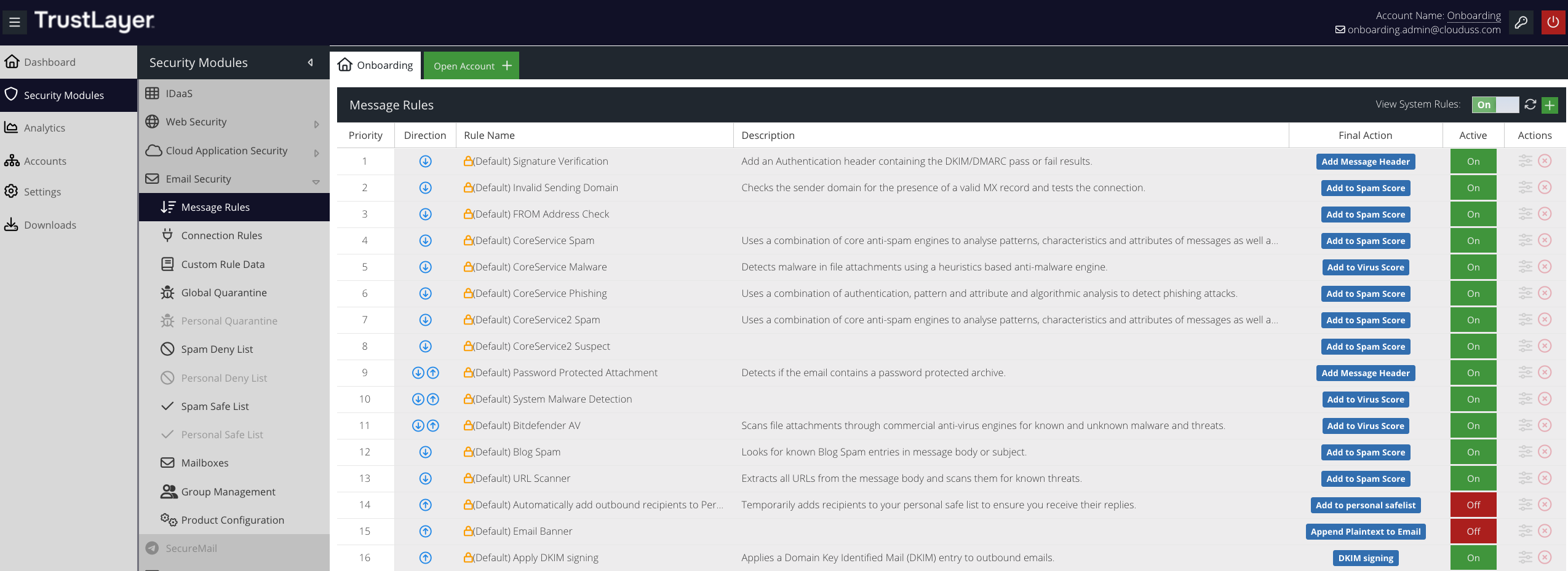
You can enable or disable a System Rule by clicking the  or
or  button in the Message Rules window.
button in the Message Rules window.
You can double-click a System Rule to view details of exactly what Conditions, Actions and Final Actions it consists of.