Administrators
Administrators are users that are created within the Unified Security Service system itself and are unrelated to any users belonging to an Active Directory connection.
Video Guide.
The video below will guide you through adding a new Administrator Account.
Creating new administrator users Step by Step.
Visit your USS Dashboard and click Products ⟶ Settings ⟶ Administrators.
To add a new Administrator, click the  button. Enter the name and email address of the new Administrator, choose the new Administrator's Role, and click
button. Enter the name and email address of the new Administrator, choose the new Administrator's Role, and click  .
.
Importing a list of new administrator users
If you have a lot of administrator users, that need to be created:
- Click
 .
. - In the dialog that appears, enter a list of email addresses (one address per line).
- Choose a Role to assign to these new administrators.
Managing administrator users
The Administrators screen shows all the Administrators that have been added to your USS account.
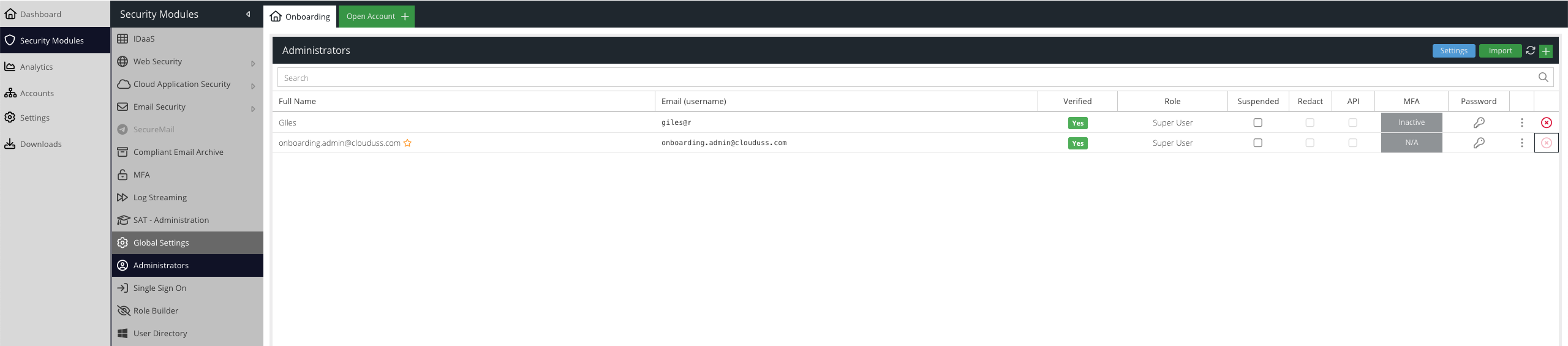
Verified
Once a user has confirmed their email address, this will be indicated here.
Suspended
A suspended user can perform no actions within the USS dashboard.
Redact
Indicates whether sensitive information within reports should be redacted, for this specific user only. To change this option click the ... button.
API
Indicates whether this user is restricted to API access only. API only users will not be able to log in to the dashboard. API users should be used for scripts and best practice is to limit them by role. To change this option click the ... button. If Multi-Factor Authentication is enforced for all users, you may need to use an API user to allow installation of agents.
MFA
Indicates whether this user has enabled Multi-Factor Authentication for access to the USS dashboard, e.g. SMS or TOTP.
- N/A - this is your own user and you cannot modify it from this location. Use the Account Password & MFA section instead.
- Inactive - the user has not yet configured a second factor
- Disable - the user has a second factor active. Click this button to disable it. You will be required to authenticate using your chosen second factor.
Password
Click the key icon to change this Administrator's password.
Deleting an Administrator
To permanently delete an Administrator, click the  icon.
icon.
Roles
An Administrator must be assigned a Role. The Role allows you to extend RBAC (Role-based Access Control) over your Cloud USS account. Each role (with the exception of the Super User role) will restrict the Administrator to specific functions and abilities within the Cloud USS Dashboard.
For a full list of roles please see the Roles Knowledge Base article.
Two Factor Enforcement
It is possible to enforce the use of two-factor authentication for your administrator users. If your account has provisioning rights, this can also be applied to child accounts.
Click the Settings button within Products -> Administrators:
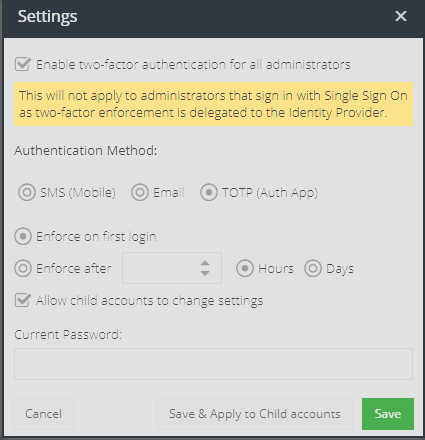
- Enable two-factor authentication for all administrators - check this box to enable enforcement
- Authentication Method - select the required method
- Enforce on first login - this will enforce the administrator user to enrol in two-factor authentication on their next login. They will be required to use SMS based second factor and can then enable TOTP (Authenticator App) afterwards if they prefer.
- Enforce after - this will apply the two-factor enforcement after the given hours (max 24) or days (max 30).
- Allow child accounts to change settings - if your account has provisioning rights, this option controls whether child accounts can override the enforcement settings.
- Current Password - You must provide your current administrator password when changing these settings.
- Save & Apply to Child Accounts - if you make changes and want to push them to any existing child accounts immediately, then click this button.